A Front-End Must-Have: Master HTTP Request Headers to Boost API Efficiency
Mastering HTTP request headers is crucial for optimizing API efficiency. This article explores key headers like Authorization, Content-Type, and Cache-Control, demonstrating how they impact performance, security, and functionality.
Hi, I’m Lee. A Front-End Dev With a Love for Clean Code & Weird Bugs.
Today, I’m not writing poetry.
I’m telling you the story of my daily adventures through the world of HTTP request headers —
one header at a time, one awkward bug at a time.
Login & Token Business (Content-Type, Accept, Authorization)
9 AM — Morning coffee brewed, time to log into our admin panel.
I send a POST request to the backend like this:
POST /api/login
Content-Type: application/json
Accept: application/json
Content-Type: “I’m sending you JSON. Treat it with care.”Accept: “Only talk back to me in JSON. No HTML nonsense.”
Backend replies with a shiny new JWT token. From now on, every authenticated request will include:
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR...
Basically: “It’s me, Lee. The verified one. Let me in.”
Getting My Profile (Authorization, Accept-Language, User-Agent)
User logs in and lands on their profile page. I send:
GET /api/user/profile
Authorization: Bearer eyJhbG...
Accept-Language: en-US, fr-FR;q=0.8
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 13_2_1)
Authorization: “Here’s my token. I’m still me.”Accept-Language: “Please give me responses in English. French is also okay-ish.”User-Agent: “I'm using Chrome on a Mac. Tailor responses accordingly.”
Backend figures I’m on desktop, returns optimized data, and logs my visit for analytics.
Profile Picture Upload (Content-Type, Content-Length, Authorization)
3:00 PM — Time for a Fresh New Avatar.
A user decides it’s time for a profile glow-up. So I fire off an image upload request:
POST /api/upload-avatar
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary
Content-Length: 389287
Authorization: Bearer eyJhbG...
Content-Type: “Hey server, this isn’t plain JSON — it’s a mashup of text fields and a file.”Content-Length: “Heads-up: this file weighs in at 389KB. Hope that’s within your upload budget.”Authorization: “Only logged-in users get upload privileges. Here's my VIP pass.”
On the backend, unpacks the file, saves it to cloud storage, and updates the user profile.
Result? A shiny new avatar and no server complaints. Everyone wins — especially the user's cat, now proudly featured.
Cached Image Drama (If-Modified-Since, Cache-Control)
Next day, user logs in again. Their profile image loads, but I want to save bandwidth:
GET /uploads/avatar-johnny.jpg
If-Modified-Since: Wed, 03 Jun 2025 10:00:00 GMT
If-Modified-Since: “Only send the image if it’s changed since June 3rd.”
Backend replies:
304 Not Modified
Browser loads the image from cache — super fast, zero server stress.
The server also sends this:
Cache-Control: max-age=86400
“Cache this for 24 hours. Don’t bug me again till tomorrow.”
Localhost, CORS & You (Origin, Referer, X-Requested-With)
While running my frontend on localhost:5173, I make a call to our API server. The browser automatically includes a few headers behind the scenes:
Origin: http://localhost:5173
Referer: http://localhost:5173/dashboard
X-Requested-With: XMLHttpRequest
Here's what they mean:
Origin: “Hey server, this request is coming fromlocalhost:5173.”Referer: “Specifically from the/dashboardpage.”X-Requested-With: “This isn’t your grandma’s form — it’s an AJAX call.”
The backend checks the Origin against its CORS allowlist. Since localhost:5173 is allowed, everything goes smoothly — no CORS errors, no angry devs.
Where’s the Traffic Coming From? (User-Agent, Referer)
My boss is nosy: “Are people using mobile or desktop more?”
So I peek at our logs:
User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 17_0 like Mac OS X)
Referer: https://www.google.com
User-Agent: “Someone visited using an iPhone — better show mobile UI.”Referer: “They came from a Google search.”
I send marketing a Slack:
“iOS + Google is our top traffic duo this week. Let’s run with that.”
Connection Management & Rate Limits (Connection, Host)
Our product catalog loads 8 widgets at once. So I fire off multiple concurrent requests:
Connection: keep-alive
Host: api.ourapp.com
Connection: “Let’s reuse the same TCP connection. It’s faster.”Host: “We’re talking to api.ourapp.com, just so you know.”
But I went a bit too wild. Server hits me back with:
429 Too Many Requests
So I add a delay and batch my calls. Lesson learned:
Even machines need breathing room
Anti-Leech Defense (Referer, Origin)
One day we notice a sketchy third-party site hotlinking our image assets.
Their requests come in like this:
Referer: http://some-sketchy-site.com
Origin: http://some-sketchy-site.com
Backend sees the headers and slams the door shut:
403 Forbidden
“Nice try. You're not allowed to steal our stuff.”
Hotlink blocked. Bandwidth saved. Justice served.
Lee’s Survival Map of HTTP Request Headers
| Scenario | Key Request Headers | Why It Matters (Business Impact) |
|---|---|---|
| User Login | Content-Type, Accept, Authorization |
Secure auth + tell server how to parse your data |
| Fetch User Profile | Authorization, Accept-Language, User-Agent |
Personalization: authenticate, localize & device adapt |
| Uploading Images | Content-Type, Content-Length, Authorization |
Securely handle large file uploads without surprises |
| Cache Control | If-Modified-Since, Cache-Control |
Speed up load times & reduce server bandwidth usage |
| Local Dev & CORS | Origin, Referer, X-Requested-With |
Validate cross-origin calls & identify AJAX requests |
| Traffic Analytics | User-Agent, Referer |
Understand visitor devices and traffic sources |
| Connection Mgmt | Connection, Host |
Keep connections efficient & route requests properly |
| Anti-Hotlinking | Referer, Origin |
Protect assets by blocking unauthorized external use |
Headers Are the Swiss Army Knife of HTTP
- They support endless use cases: login, language preferences, file uploads, cache validation, CORS, and even resuming downloads.
- They boost performance & security: like reducing bandwidth with caching headers, or locking down endpoints with authorization headers.
- They keep HTTP future-proof: via custom headers and protocol extensions — the web keeps evolving, and headers keep up.
Headers aren’t just technical garnish — they’re the grammar of client-server conversations. And the more fluently you speak it, the smoother your APIs will run.
Let EchoAPI Handle the Header Headache
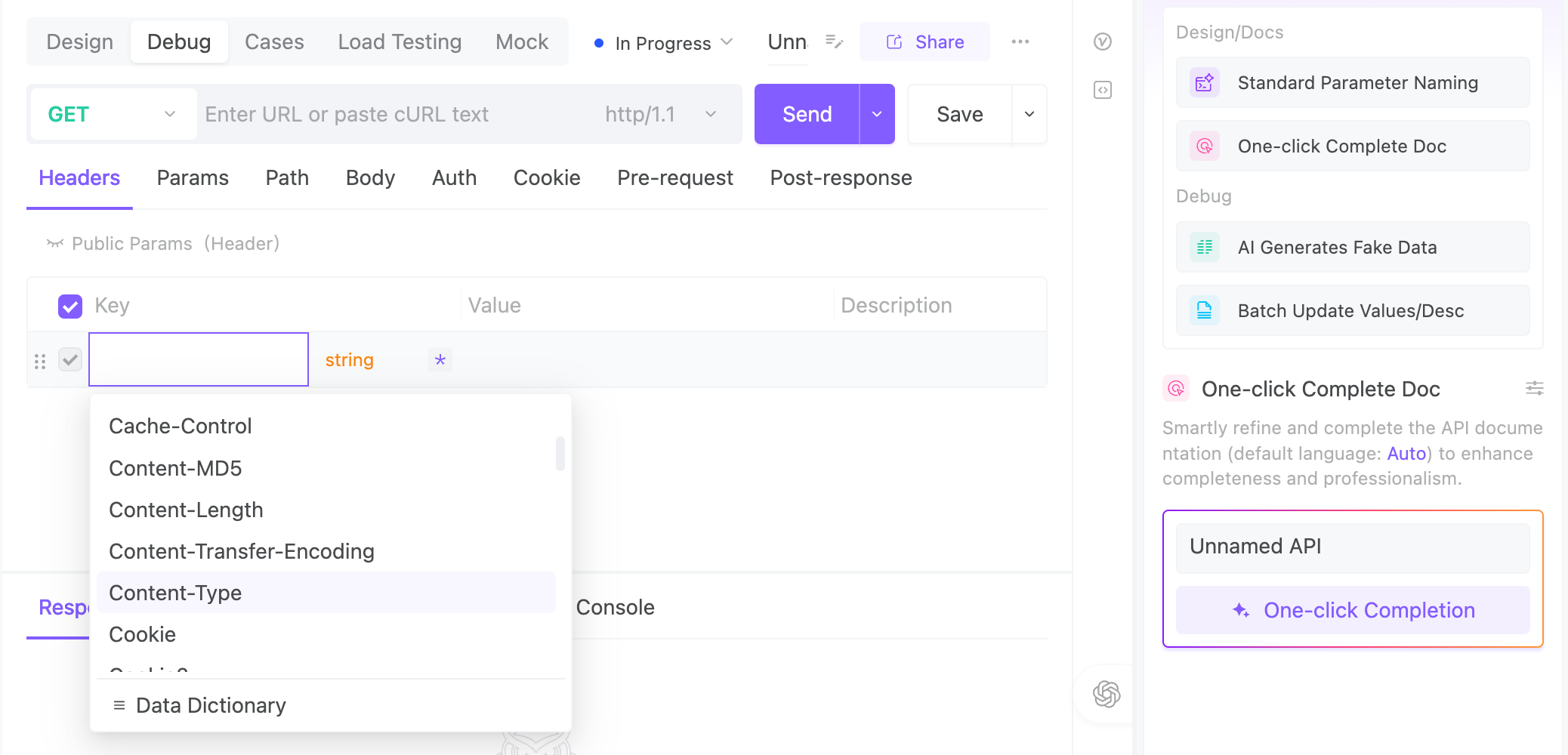
Setting all these headers manually can be, well... kind of a nightmare.
Between authentication tokens, content types, cache control, and CORS gymnastics, it’s easy to lose track of what’s what.
That’s where EchoAPI shines.
- Simulate real-world API requests — complete with all the right headers
- Debug any kind of endpoint — from login auth to custom enterprise APIs
- Improve test coverage — by controlling headers precisely and exploring more scenarios
- Make team collaboration easier — share exact request setups across teams
- Stay ready for what’s next — with support for custom headers and emerging standards
In short, EchoAPI gives you the master key to test smarter, faster, and with more confidence.
Ready to Level Up Your Header Game?
Use EchoAPI to turn guesswork into clarity, chaos into control, and headers into your best debugging ally.
Because when your headers speak clearly, your APIs respond better.




 EchoAPI for VS Code
EchoAPI for VS Code

 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








